
Bridging IT and OT Security Gaps
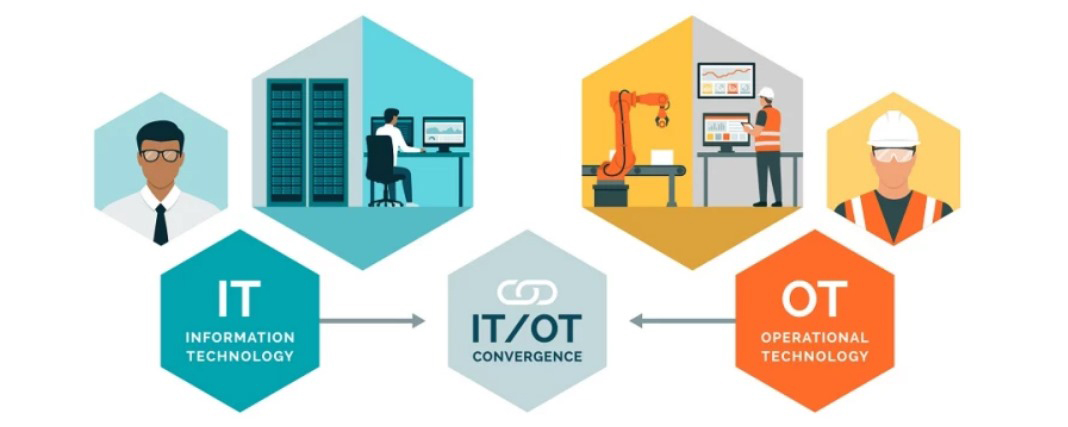
In the evolving digital landscape, operational technology (OT) systems like those found in manufacturing, energy, and transportation are increasingly connected to IT networks and cloud platforms. While this integration boosts efficiency and enables real-time analytics, it also opens the door to cyber threats. Traditional OT systems were not designed with internet connectivity in mind, making them highly vulnerable. A strong cyber security framework is essential to bridge this gap, ensuring both IT and OT systems can coexist without compromising safety or performance.
OT/IoT Cyber Security
Our cloud solutions are more than just a migration; they represent a paradigm shift in how businesses leverage technology to drive innovation and agility. With us, you embark on a transformative journey, leveraging the cloud's scalability, flexibility, and efficiency to propel your organization into the digital age. Our cloud services are tailored to align your business objectives with the right cloud solutions while minimizing disruptions and enhancing scalability. We continuously monitor, manage, and optimize your cloud infrastructure, increase efficiency, enhance time-to-market, and deploy reliable infrastructure.
Cloud Solutions
A holistic approach to cyber security is necessary to defend against sophisticated attacks that exploit both cloud and OT vulnerabilities. Unified Threat Management (UTM) systems, which integrate firewalls, intrusion detection, and anomaly monitoring, provide real-time visibility and control across all digital assets. When combined with AI-driven analytics and a Zero Trust architecture, these systems help detect anomalies early, respond faster, and reduce downtime. Ultimately, aligning security strategies across cloud and OT environments ensures robust, end-to-end protection.
As manufacturers connect their OT / IOT systems to IT systems and networks as part of their digital transformation (Industry 4.0) they need to ensure they do it securely and apply OT / IOT security best practices. Unlike IT which processes an organization’s front-end informational activities, OT is focused on back-end production. Securing an organization’s industrial operations is vital for industries engaged in activities such as manufacturing.
Fostering frictionless workflows with cyber secure access to OT / IOT is critical in this sector. Solutions need to be able to secure any protocol, any access, local or remote while respecting production needs. No more providers connecting via unidentined gateways, no more clear passwords in production. No more third-party operators connecting to retrieve backups for other customers. more control, traceability and operational efficiency. Because OT / IOT performance is instrumental to the company's business, particular attention must be paid to securing OT / IOT assets.

Empower your business with precision-driven automation and monitoring
At StackEx Private Limited, we help businesses unlock peak efficiency through precision driven automation and intelligent monitoring solutions. Our custom-built systems offer real-time insights, enhanced control, and seamless integration ensuring optimized performance across every stage of your operations.
Get Started
